Ransomware doesn’t just appear out of nowhere: it follows a clear and calculated strategy. The Kill Chain of a Ransomware Attack describes each phase an attacker goes through, from the first contact with the victim to the execution of the malware and the subsequent extortion.
Understanding this process is not only key to knowing how a compromise unfolds, but also to identifying critical defense opportunities and implementing effective controls at every stage.
Here are the typical phases of a ransomware kill chain:

Understanding this process allows you to anticipate their moves and strengthen your defense strategy by placing specific controls at each critical stage.
The earlier you identify an attempted compromise, the greater your chances of stopping the attack before it causes real damage.
In the world of cybersecurity, those who understand the process master prevention. Don’t let your organization be the next to fall into the ransomware trap!
🔍 1. Reconnaissance
The attacker gathers information about the target. This may include:
Scanning ports and services.
Analyzing social media.
Collecting email addresses.
Searching for leaked credentials on the Dark Web.
🔐 Objective: Identify weak points and potential access methods.
🚨 Exfiltrating corporate VPN credentials: Uber Hacking Incident (2022) Possibly originating from a previous leak or purchase on the Dark Web, combined with MFA fatigue attack techniques (bombarding the user with MFA push notifications until they mistakenly approve one).
📩 2. Delivery
The attacker deploys the ransomware into the system. Common methods include:
Phishing (emails with malicious attachments or links).
Downloads from compromised websites (drive-by-download).
Exploiting vulnerabilities in exposed services.
🧪 Objective: Infiltrate the initial payload without being detected.
🚨 The main technical vulnerability historically exploited by ransomware for propagation is: Vulnerabilities in the SMB (Server Message Block) protocol, especially EternalBlue (CVE-2017-0144).
The famous ransomware attacks, WannaCry (2017) and NotPetya (2017), exploited this vulnerability to spread massively and automatically.
🚪 3. Execution
The malicious code is executed on the compromised system. This can happen through:
Macros in documents.
Automated scripts (PowerShell, etc.).
Misuse of legitimate tools (living-off-the-land techniques).
💣 Objective: Gain control and persistence within the system.
🚨 Why are administrative privileges a major mistake when facing ransomware?
In ransomware attacks like Ryuk, Conti, or LockBit, once a user machine with administrative privileges was compromised:
The malware deployed PowerShell scripts to disable EDRs (Endpoint Detection and Response) and antivirus solutions.
It encrypted shared folders massively by leveraging privileged credentials.
It moved laterally using administrative tools such as PsExec or WMIC.
🎮 4. Command & Control - C2
The ransomware establishes communication with the attacker’s servers:
To receive instructions.
To download additional modules.
To send victim information.
🌐 Objective: Maintain remote control of the infected system.
🚨 Modern ransomware heavily relies on tools like Cobalt Strike and Sliver for Command and Control (C2), using HTTPS, DNS, and encrypted tunnels to remain hidden.
Conti ransomware: Used Cobalt Strike beacons to move laterally and maintain control even when internal credentials were changed.
LockBit: Used Ngrok tunnels to create C2 channels that were difficult to detect within normal HTTPS traffic.
Black Basta: Migrated to using Sliver to evade signature-based detections of Cobalt Strike.
Ryuk: Initially operated with Metasploit and later migrated to Cobalt Strike.
📦 5. Lateral Movement and Privilege Escalation
The attacker explores the internal network, accesses other devices, and looks for:
Additional credentials.
Critical servers or backups.
🧭 Objective: Expand the reach of the attack.
🚨 Attack flow: In the Conti ransomware campaign, attackers used stolen credentials and lateral movement techniques with Cobalt Strike and PsExec, relying on tools like Mimikatz to escalate privileges and compromise entire networks before deploying ransomware:
Initial access: They accessed a machine via RDP using weak or leaked passwords.
Privilege escalation: They ran Mimikatz to obtain administrator credentials from the machine.
Lateral movement: With admin credentials:
They connected to other servers using PsExec.
Abused SMB to spread malicious payloads.
Used Rubeus to steal Kerberos tickets and access additional resources.
Full compromise: Once they had control over most of the infrastructure, they launched mass encryption.
🔒 6. Encryption & Exfiltration
Files are encrypted and, in many cases:
Information is exfiltrated before encryption.
Local or remote backups are deleted.
🔐 Objective: Leave the organization without access to its data.
🚨 Modern ransomware uses legitimate tools like Rclone, WinRAR, 7-Zip, MegaCMD, Ngrok, FTP/SFTP, and encrypted tunnels (such as plink.exe) to steal data before encrypting it.
Conti Ransomware: Used Rclone to exfiltrate data to cloud servers before encryption.
LockBit: Used WinRAR to package stolen databases and then transferred them via FTP.
BlackCat (ALPHV): Employed Ngrok and MegaCMD to transfer large files without leaving direct traces on the internal network.
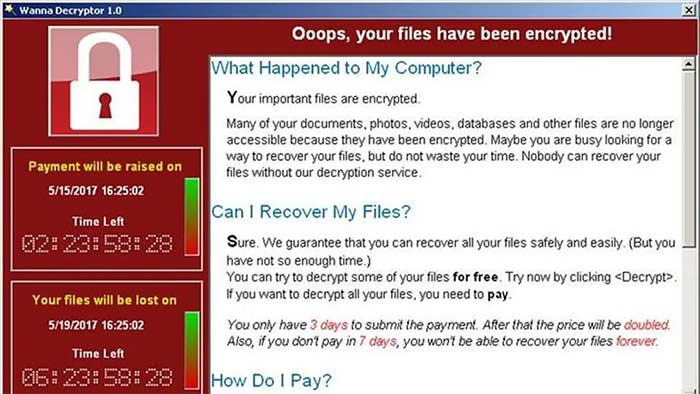
💰 7. Ransom Demand
The ransom note is displayed:
A payment is demanded (usually in cryptocurrencies).
Victims are threatened with data exposure if they do not pay.
💸 Objective: Obtain financial gain.
🧩 BONUS: Persistence
Some attackers leave backdoors behind for a second attack or to ensure payment if the victim attempts to restore without paying.